
Synopsis: The Cisco Federal Operational Security Stack streamlines the process for Cisco SaaS solutions on their FedRAMP journey, bringing a myriad of benefits. It revolutionizes product engineering team workflows by…

Synopsis: The Cisco Federal Operational Security Stack streamlines the process for Cisco SaaS solutions on their FedRAMP journey, bringing a myriad of benefits. It revolutionizes product engineering team workflows by…

AI is moving quickly, which means more risks: data vulnerabilities, cyberthreats, and ransomware attacks. Protecting the AI runtime from manipulation, preventing model theft, and preventing training data poisoning should be…

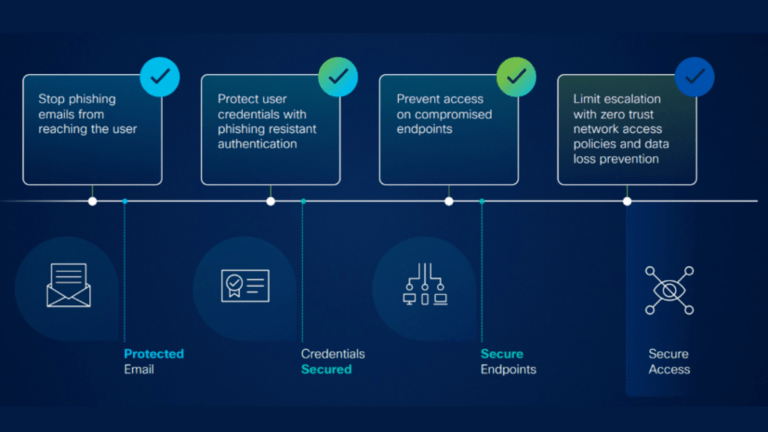
Phishing remains a significant component of the cyber threat landscape due to its simplicity, effectiveness, and adaptability. It is a deceptive practice in which threat actors pose as legitimate entities in…

The experience of a breach has significant impact on how an organization approaches resilience. Unfortunately, breaches are far too common, affecting companies of all sizes across all industries. Like any…

The landscape of Web Application and API Security is undergoing a rapid evolution, demanding WAF services to be better equipped to handle modern development tools and keep up with the…

Bristol Myers Squibb (BMS) is a global biopharmaceutical giant with over 30,000 employees dedicated to advancing medicine. BMS focuses on oncology, hematology, immunology, and cardiovascular disease, aiming for groundbreaking treatments.…

Finance is evolving towards always-on and ubiquitous services. In the future, financial institutions need to build a robust and resilient financial digital infrastructure that follows the 4 Zeros. The rapid growth…

Just as our digital adversaries work together to advance their attack methods, no single organization alone can successfully disrupt cybercrime at scale. Fortinet has a long history of collaborating with…

The average dwell time – an attacker’s time in your environment before detection or executing their attack – is 204 days. For nearly seven months, attackers move around stealthily, discovering valuable…

Major sporting events like the World Cup, Super Bowl, and Wimbledon attract millions, even billions, of viewers. Argentina’s shootout win over France in the final game of the Qatar 2022…

In the last few hours, major disruptions on CrowdStrike’s Falcon platform causing significant productivity impacts due to inaccessible documents have been reported. The CrowdStrike Falcon update has led to a…

Getting ahead in a world where disruption is the norm requires seamless access to data, no matter where it lives. Cloud is no longer a separate IT initiative, but often,…

In recent years, the telecommunications industry has been at the forefront of adopting cutting-edge technologies to enhance operational efficiency, improve customer service, and innovate in service offerings. Now, the industry…

On July 1, 2024, the Qualys Threat Research Unit (TRU) disclosed an unauthenticated, remote code execution vulnerability that affects the OpenSSH server (sshd) in glibc-based Linux systems. [For more information…

Solving customer issues quickly, accurately and effectively on a global scale with new GenAI tools powered by GPT-4 Lenovo’s AI solution helps human experts improve the speed, accuracy and quality…

You probably hear the terms “cybersecurity” and “cyber resilience” used quite a bit, especially as cyberthreats become increasingly common—and costly. These terms don’t describe exactly the same thing, and there…
The Dinner Party Supply Chain Attack A supply chain attack occurs when a bad actor gains access to an organization’s people and data by compromising a vendor or business partner.…

AI is going from strength to strength and is beginning to spur transformative change in industries from finance to healthcare to education and beyond. A sort of rhythm has been…
We recently hosted the annual NetApp Industry Analyst Summit in New York City, bringing together some of the best thinkers in our industry. In one session about the incredible amount…

As evident with Commvault’s recent Secure by Design Pledge, we are committed to providing our customers with a secure platform to help manage risk and remain resilient in today’s digital…
Every industrial manufacturing conference you attend highlights all the possible business benefits and workloads associated with Industry 4.0: the convergence of operational technology (OT) and information technology (IT). Benefits that…

The cloud is a fantastic way to deliver a multitude of services, but it’s equally important to recognize when a purely cloud approach can be sub-optimal. That’s why Harmony SASE…

Workload security tools draw the attention of diverse cohorts, united by a mission: fortifying hybrid cloud workloads. In a market filled with disparate tools, Secure Workload offers a tailored reporting…
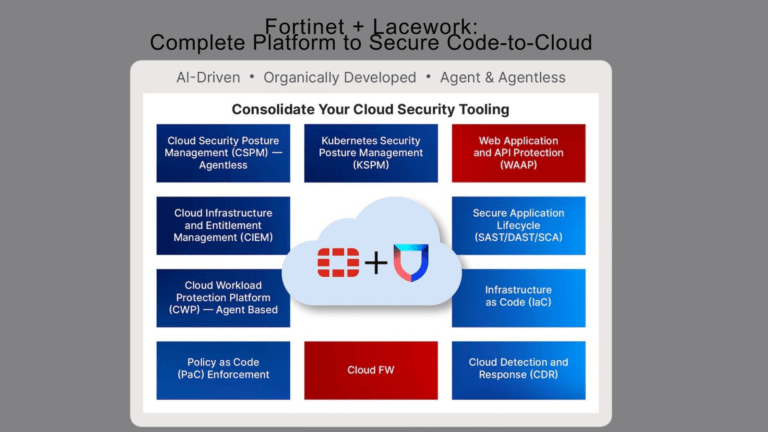
Most customers will have hybrid infrastructure for the foreseeable future. Users are moving in and out of the office, more IoT and OT devices are connected, networks have more edges…

In today’s digital landscape, ensuring the security and compliance of sensitive data is of paramount importance, especially for government organizations. Commvault recognizes this critical need and has achieved a significant…
© 2024 Created By YouDream Consulting