
The ready-to-use AI-ready stack featuring FlexPod® AI is designed to meet the needs of enterprise generative AI (GenAI) applications. It combines Cisco computing power, NetApp® storage solutions, NVIDIA GPUs, and a range…

The ready-to-use AI-ready stack featuring FlexPod® AI is designed to meet the needs of enterprise generative AI (GenAI) applications. It combines Cisco computing power, NetApp® storage solutions, NVIDIA GPUs, and a range…

Developer experience changes rapidly. Many developers and the Cisco DevNet community utilize Generative AI tools and language models for code generation and troubleshooting. In the article, “How To Get Started…
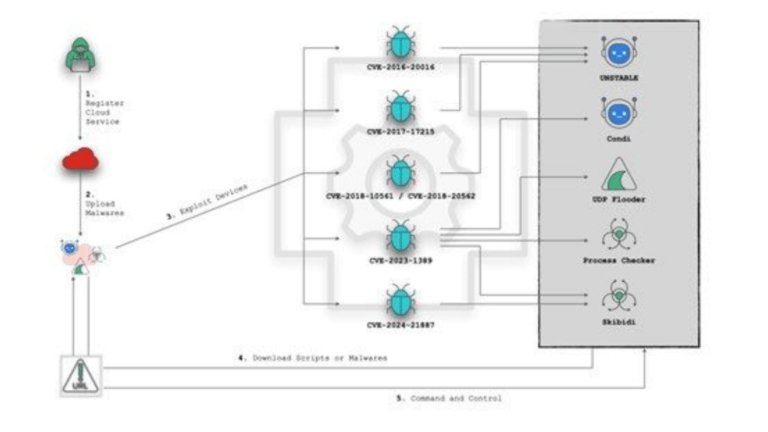
Cybersecurity threats are increasingly leveraging cloud services to store, distribute, and establish command and control (C2) servers, such as VCRUMS stored on AWS or SYK Crypter distributed via DriveHQ. This shift in strategy presents…

In our connected world, the widespread adoption of technology has revolutionized the way organizations deliver data-based services. Whether it’s consumers relying on online platforms or governments serving citizens, the importance…

A sophisticated new malware/trojan attack is designed to steal login credentials and credit card information from payment systems, banks and crypto exchanges. This attack tricks legitimate business applications into running…

Running 100KW+ server racks without the need for specialized data center air conditioning with 6th Generation Lenovo Neptune This week, Lenovo announced the 6th generation of Lenovo Neptune™ liquid cooling, designed to help businesses…

Everyone is talking about data security and its importance, but what does that practically look like? Let’s take a look… Our newly released Cloud Security Report showed a startling trend in the…

One Phish, Two Phish, Spy Phish, AI Phish: How Email Scams Got Smart If only things were this easy. There’s never been a time where phishing was good, but there…
In an ever-evolving digital landscape, cybersecurity has become the cornerstone of organizational success. With the proliferation of sophisticated cyber threats, businesses must adopt a multi-layered approach to ensure the integrity…

In my last blog, I shared the progress we’re making toward building the Cisco Security Cloud, an open, integrated security platform capable of tackling the rigors of securing highly distributed, multicloud environments.…
Cloud Computing provides us with flexibility in creating and scaling workloads, but it also opens up new challenges when we become habitual with cloud characteristics. One of the examples is…

5G has fulfilled its mission of enabling connectivity of everything. As the foundation of the digital economy, it has redefined what communications mean for billions of users, tens of millions…

Organizations must strive for cyber resilience to meet increasing requirements for cybersecurity regulations. Companies in 2024 will adopt more proactive risk management strategies to not only attempt to thwart malicious…


For the DreamWorks Animation team behind the latest installment of the Kung Fu Panda franchise, animating The Chameleon posed just as big of a challenge. But just like the mimicking reptile herself,…
Circularity means different things to different people. No one business is at the same stage when it comes to sustainability, and this means a range of solutions are required to…

This is part two of a multi-part blog series on AI. Part one, Why 2024 is the Year of AI for Networking, discussed Cisco’s AI networking vision and strategy. This blog will…
© 2024 Created By YouDream Consulting