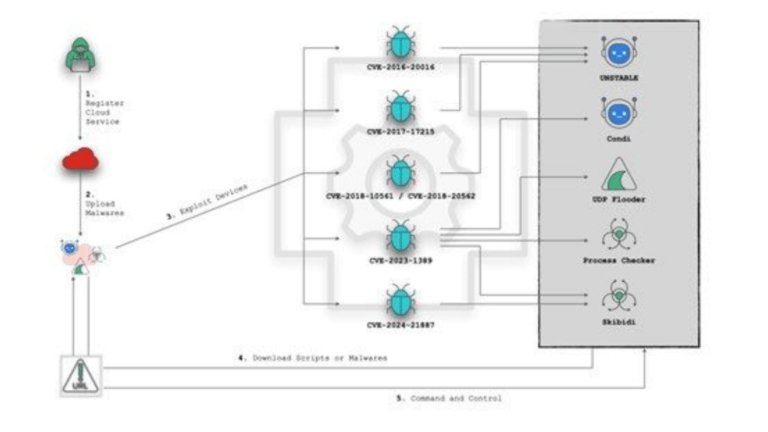
Cybersecurity threats are increasingly leveraging cloud services to store, distribute, and establish command and control (C2) servers, such as VCRUMS stored on AWS or SYK Crypter distributed via DriveHQ. This shift in strategy presents significant challenges for detection and prevention, as cloud services provide scalability, anonymity, and resilience that traditional hosting methods lack.
Over the past month, FortiGuard Labs has been monitoring botnets that have adopted this strategy, abusing cloud services to enhance their malicious capabilities. These botnets, such as UNSTABLE and Condi, have been observed leveraging cloud storage and computing services operators to distribute malware payloads and updates to a broad range of devices […]